Gain comprehensive insight into third party risk with versatile risk assessment tiers, from OSINT to questionnaires to full internal security assessments.
get more from tpcrm.
get more from tpcrm.
get more from tpcrm.
get more from tpcrm.
get more from tpcrm.
get more from tpcrm.
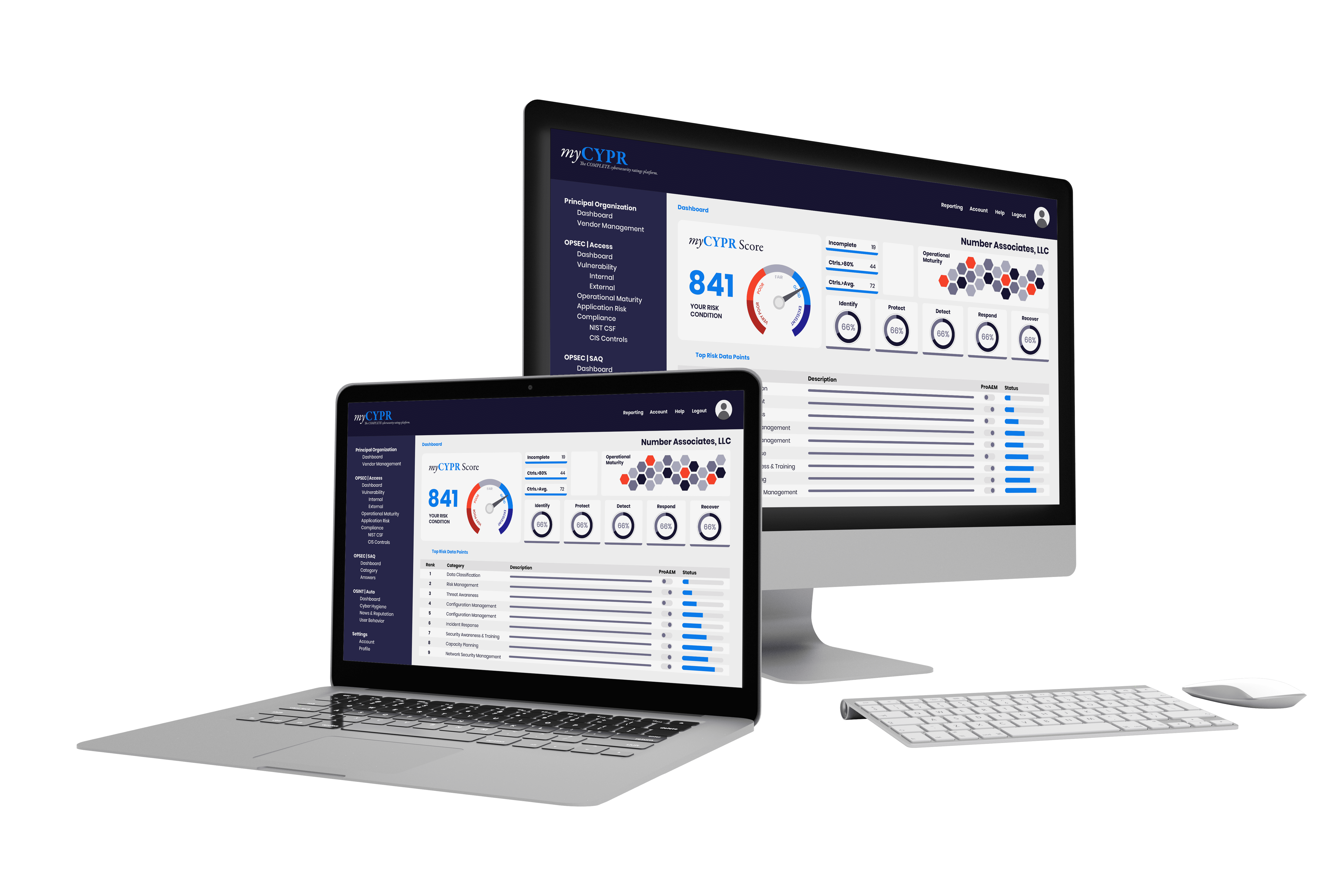
Organizations need more risk data to make informed decisions. Choose between our OSINT risk scoring, vendor security questionnaire, and internal security risk assessment tiers to best match your third party relationships.
Opt for standard OSINT risk insight for low risk vendors, or ask for more from the relationships that have more on the line.
See to Secure
If you can’t see the problem to identify the risk, you can’t manage it. Traditional risk assessments alone have proved too much for effective vendor management, while current OSINT-based risk scoring solutions don’t seem to be enough for managing an organization’s total risk profile.
myCYPR bridges the gap by providing options for everything in between in one consolidated platform.
the data
Why does Choice Matter?

Good
OSINT | Auto
Cyber Hygiene, News & Reputation, User Behavior
OSINT-based risk assessments are used as the sole basis for many of today’s cyber risk management solutions. This publicly sourced data has its value, but cannot capture the full scope of risk facing an organization on its own.
OSINT is optimal for assessing risk with new business potential, vendors who are not critical to operations, or vendors with limited access to sensitive data. OSINT | Auto offers a quick, inexpensive view of possible indicators of risk and is updated weekly.
Risk
Management

Better
OPSEC | SAQ
99 Questions | Risk Management Evaluation | Evidence Collection
Self-Assessment Questionnaires lose value when every questionnaire is different. When some vendors submit restricted multiple-choice selections and others provide broad, open-ended responses, they become as painstaking to review as they are to fill out. While questionnaires are guided by similar controls, there are no true standards dictating what should be assessed.
myCYPR’s SAQ focuses on 25 key areas of cybersecurity posture from common standards, including the NIST Cybercesurity Framework and the Center for Internet Security’s Critical Security Controls. Responses are standardized for consistency between vendors but remain flexible with options to acknowledge risk, note plans for remediation, and provide evidence. Responses can be assigned to up to 3 participants per organization for validation and improved accuracy and are easily shared between organizations.
Risk
Management

Best
OPSEC | Assess
Internal & External Vulnerability | Operational Maturity | Application Risk
Traditional security assessments offer the greatest degree of insight, but the time and cost required prevent it from being a practical option for vendor management. Results are also difficult to identify and prioritize, concealed within lengthy paper reports that are difficult to consume.
OPSEC | ASSESS identifies risk through security assessments and detailed gap analysis mappings to NIST and CIS frameworks. Detailed remediation recommendations are provided and myCYPR security consultants collect and review evidence for increased accuracy. The degree of data collection is like that of traditional assessments, but the digital dashboard ensures results are easy to find, prioritize, and remediate.
Risk
Management
Build your TPCRM program
Multiple factors help determine the appropriate level of risk assessment for your vendors. By selectively employing various assessments tailored to each vendor, you can construct a robust, custom TPRM program.
Vendors
To start, identify all active or potential vendors in your third-party network.
Data
Establish each vendor’s data relationship based on their access level to sensitive data.
Power
Determine vendor power dynamics, like their importance, mutual dependence, etc.
Budget
Consider the total budget available and determine how much is allocated per vendor.
Group
Categorize vendors with similar dynamics, like importance, power, or data relationships.
Assessment
Define TPCRM program by selecting the level of assessment appropriate for each group.
How does myCYPR protect you?
Increase Visibility Of Risk Data
Automate Risk Monitoring
Common Standard Of Security
Vendor Trust & Transparency
Why it Works
Visibility For First- And Third- Parties
Alleviate Resource Constraints
Exceed Compliance Requirements
Adaptable To Risk And Budget Requirements
Ready to bridge the gap in TPCRM with us?
Schedule a demo to learn more about enhancing the management of your third parties with myCYPR.